Evolution of Financial Identity Risks
From Stolen Wallets to Hacked Wallets
A few decades ago защита личных данных was mostly about not losing your physical wallet. Financial identity theft meant someone got hold of your checkbook, your card, or maybe raided your mailbox.
Then came large-scale digitization of banking, e‑commerce, and credit systems. Suddenly:
– Card-present fraud shifted to card-not-present (online) fraud
– Social Security numbers and national IDs started circulating in huge databases
– Credit bureaus centralized data, making them attractive targets
Major breaches (like Equifax in 2017) showed that even if you personally behave perfectly online, your financial identity can still leak via third parties. That’s why identity theft protection services and credit monitoring platforms became a separate industry rather than just a “nice add‑on” from banks.
Case: Data Breach Fallout (Illustrative but Based on Real Patterns)
Anna never shared her card details with shady sites, used a strong password manager, and felt confident online. Yet one morning she saw two new credit cards in her credit report that she had never opened.
Investigation revealed: her data was compromised in a retailer data breach 18 months earlier. A criminal bought her full identity profile (name, address, SSN, date of birth) on a darknet market and used it to:
– Open new lines of credit
– Change contact email on one of her old bank accounts
– Attempt a small loan at an online-only bank
Anna discovered this only because she enabled credit report monitoring and identity theft insurance through her employer’s benefits program, which flagged the new credit inquiries. Without that alert, debt collectors would likely have called months later—when damage and recovery costs were much higher.
—
Core Principles of Protecting Your Financial Identity Online
Defense-in-Depth, Not Magic Tricks
Protecting your financial identity isn’t about one “silver bullet” app or gadget. It’s about defense-in-depth:
1. Reduce exposed data
2. Limit what can be done with that data
3. Detect misuse quickly
4. Respond and recover fast
These layers work together. If one fails, the others reduce the damage window.
Principle 1: Minimize Your Digital Footprint
Every extra place that stores your financial identifiers (card numbers, SSN, tax ID) is one more potential leak.
– Avoid storing card data in every small online store “just for convenience”
– Delete unused accounts on old marketplaces and fintech apps
– Use virtual or single-use cards where your bank supports them
Short version: if a service doesn’t really need your data, don’t give it.
Principle 2: Strong Authentication Everywhere Money Touches
For anything tied to payments, loans, or investments:
– Use a proper password manager
– Enable multi-factor authentication (MFA) (prefer apps or hardware keys over SMS where possible)
– Separate email: have one “money email” used only for banks, brokers, and tax services
This way, compromising a “fun” service (social media, gaming, forums) doesn’t instantly open the door to your financial accounts.
Principle 3: Continuous Monitoring and Rapid Response
Even with perfect hygiene, your data may leak via a bank, employer, or vendor. That’s why monitoring matters more than perfection.
Two main vectors:
– Account activity monitoring (transactions, login alerts, new device alerts)
– Credit file monitoring (new accounts, hard inquiries, changes of address)
The best credit monitoring service for you is the one that:
– Monitors all major bureaus relevant to your country
– Sends real-time or near real-time alerts
– Helps with recovery, not just notifications
—
Practical Ways to Implement Protection
Hardening Your Accounts Step by Step
Here’s a pragmatic sequence to secure your financial identity over a weekend.
1. Lock down email and phone
– Change email password to a long, unique one via a password manager
– Enable MFA using an authenticator app or hardware key
– Set a PIN or password for SIM swaps at your mobile operator (call support or check the app)
2. Secure online banking and investment platforms
– Turn on all available security settings (MFA, device recognition, login notifications)
– Configure alerts:
– Transactions above a small threshold
– Logins from unknown devices or locations
– Changes to contact details or passwords
3. Harden your devices
– Full-disk encryption on laptop and phone
– Biometric or strong passcode on lock screen
– Up-to-date OS and browser; auto-update enabled
– Separate browser profile (or even a separate device) for financial activities only
Short tip: if your browser profile with 50 random extensions is also used for banking, that’s a weak point.
Case: “Friendly” Device Infection
Mark, a freelancer, used his work laptop for everything: torrents, obscure plugins for “free” PDF tools, and online banking. One day, his bank started flagging strange login attempts from his usual city and device.
A remote-access trojan installed via a pirated software installer was quietly recording his keystrokes and taking screenshots. The attacker didn’t even need to bypass MFA; they waited until Mark logged in and then piggybacked on his active browser session to change his contact phone number and email.
The only reason damage was contained: Mark had enabled push notifications for every profile change and called the bank within minutes. After a full device wipe and new credentials, his accounts remained safe—but it could have easily turned into a full takeover.
—
Working with Banks and Service Providers
Configuring Online Fraud Protection for Bank Accounts
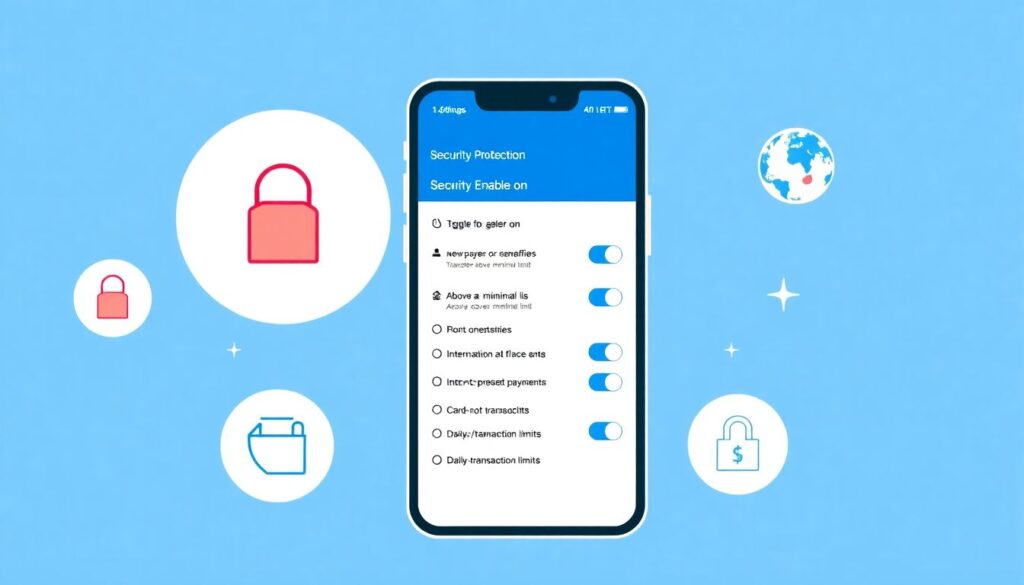
Most modern banks have built-in online fraud protection for bank accounts, but it’s only as good as your configuration.
Check and enable:
– Alerts for:
– New payees or beneficiaries
– Transfers above a minimal limit
– International transactions
– Card-not-present payments
– Daily and transaction limits for transfers and withdrawals
– Confirmation steps for sensitive actions (e.g., adding a new device, changing phone)
Also, explicitly ask your bank:
– What’s their liability policy for online fraud?
– What is the procedure if you report fraud (timelines, documents, temporary blocks)?
– Are they integrated with any identity theft protection services that offer extended support?
Using External Protection Services Wisely
Stand-alone protection products can be useful, but they differ a lot. If you want to compare identity theft protection plans, look at:
– Which credit bureaus and data sources they monitor
– Whether they include identity documents, dark web monitoring, and social media checks
– If they offer restoration services (specialist who helps you dispute charges, freeze credit, file reports)
– Coverage limits of identity theft insurance (lost wages, legal fees, not just direct fraud amounts)
Short note: don’t buy a service just because it “sounds secure.” Examine what specific risks it mitigates for *your* situation.
—
Monitoring: Credit, Transactions, and Beyond
What Credit Report Monitoring Really Does
Credit report monitoring and identity theft insurance tend to be bundled but they solve different problems:
– Monitoring: early detection (new loans, cards, or inquiries in your name)
– Insurance: helps cover the *cost of recovery* (lawyers, notarization, time off work), not usually the fraudulent purchases themselves—that’s typically covered by banks or card schemes
Key practical steps:
– Check your credit reports at least 1–2 times per year
– Freeze or lock your credit file if your country supports it and you’re not frequently applying for new credit
– Set up alerts for new inquiries where the bureau allows it
Case: Synthetic Identity and Slow-Burn Fraud
In a realistic scenario, criminals combined a child’s Social Security number with an adult’s name and address to build a synthetic identity. They started with low-limit credit, paid on time for a year, then maxed out several cards and disappeared.
The parents discovered it years later, when the now-teen tried to open a student account and was rejected for “bad credit history.” Because there had been no credit report monitoring, the fraud matured unnoticed.
Lesson: even if your kids “don’t use the internet for money,” their future financial identity can still be hijacked today.
—
Frequent Misconceptions and Hidden Traps
Misconception 1: “My Bank Will Just Refund Everything”
Banks often do a decent job with card fraud refunds, especially for unauthorized card transactions. But that doesn’t mean you’re safe in all scenarios:
– If attackers open new loans in your name, you must prove you didn’t authorize them
– Fraud investigations can drag on for months
– Your credit score may drop in the meantime, affecting your ability to rent an apartment or get a mortgage
– You’ll likely spend dozens of hours on calls, forms, and documentation
That’s why quick detection and a clear action plan are as important as refund guarantees.
Misconception 2: “I Don’t Have Much Money, No One Cares About Me”
Attackers don’t manually choose interesting-looking victims; they run automated campaigns:
– Phishing blasts to millions of emails
– Credential stuffing using leaked password databases
– Malware kits that target anyone with a vulnerable system
Your small balance still gives them:
– A real, aged identity profile they can resell
– Access to your credit line, not just current funds
– Potential lateral movement into your employer’s systems (if you mix devices and accounts)
In practice, “uninteresting” targets are often more attractive: less protected and less likely to notice small, recurring fraud.
Misconception 3: “I Installed One Security App, I’m Done”
Security tools are just *components*. Relying on a single antivirus or VPN to “solve everything” leads to a false sense of safety.
Things a VPN does not do:
– It does not stop you from giving your card details to a phishing site
– It does not protect you if someone impersonates you to a credit bureau
– It does not fix a weak, reused password or a lack of MFA
Think of tools as seatbelts and airbags—not as permission to drive blindfolded.
—
Real-World Style Playbook: What to Do Right Now
Immediate Actions You Can Take This Week
To put all of this into practice, focus on a practical checklist:
– Secure email and phone (password manager, MFA, SIM protection)
– Turn on all possible alerts in your online banking and card apps
– Separate your “financial” digital identity (dedicated email, cleaner browser profile)
– Review which services store your cards; delete unnecessary saved cards and accounts
– Obtain and review your credit report; set up monitoring or a credit freeze if appropriate
Short, but important: document your baseline now. Take screenshots or PDFs of your current credit report and account settings. If something changes later, you’ll have evidence.
If You Suspect Financial Identity Abuse

If you notice something odd—unknown transactions, letters about loans you never requested, or new account confirmations—act fast:
1. Contact the bank or issuer immediately and request a freeze or temporary block
2. Change passwords and revoke active sessions for affected services
3. Check your credit reports for unfamiliar accounts or inquiries
4. File necessary reports (police, regulator, or consumer protection agency, depending on jurisdiction)
5. Consider onboarding with one of the identity theft protection services that can help coordinate recovery
Time is your most valuable asset in these cases. The sooner you react, the smaller the blast radius and the easier the cleanup.
—
Final Thoughts
Protecting your financial identity online is less about paranoia and more about structured habits:
– Minimize where your financial data lives
– Lock down the core accounts and devices that control your money
– Add monitoring and alerts so nothing major happens silently
– Have a simple, rehearsed plan for what to do if something feels off
Online financial systems are powerful, and yes, fragile. But with a layered approach and a bit of discipline, you dramatically reduce both the odds of serious identity theft and the cost of dealing with it if it does happen.

